IT infra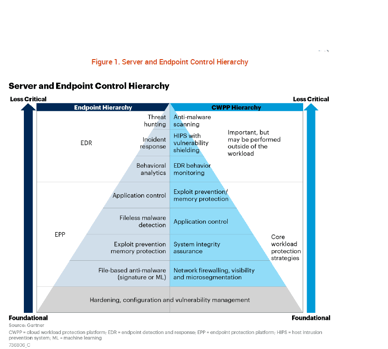 structure has evolved considerably over recent years, but security considerations have remained static for many organisations. As first enterprise workloads have moved out of the organization to the cloud and then increasingly due to Covid, endpoints have moved from the office to the home, security remains largely focused on protecting the perimeter of the organization.
structure has evolved considerably over recent years, but security considerations have remained static for many organisations. As first enterprise workloads have moved out of the organization to the cloud and then increasingly due to Covid, endpoints have moved from the office to the home, security remains largely focused on protecting the perimeter of the organization.
In addition, traditional servers have been transformed into Cloud workloads, containers and agile development apps platforms, however, it is still common practice to approach this new IT infrastructure with the same security solutions that are deployed for endpoint devices, according to a recent Gartner Report
A user endpoint device is routinely exposed to threats from email downloads, malicious links and application updates. In contrast, server workloads usually have a predictable and predefined set of processes and activities, where implementing a default-deny approach can help prevent the execution of untrusted processes. As the whitepaper explains, with more agile development and deployment of server workloads, especially in hybrid multi-cloud environments, security controls diverge even further.
Save now, repent at leisure
As Gartner explains, the risk priorities are different in both cases. Regional security and risk management leaders, therefore, need to take a fresh look at security practices to avert the financial and reputational damage that comes with increasingly frequent and more sophisticated attacks seen today.
Inadequate security solutions may reduce short-term outlay, but the damage control from data breaches can prove significantly more expensive. In 2020, the average data breach incident in the Middle East cost $6.53 million, nearly double the global average incident cost of $3.86 million, according to the Ponemon Institute. The region currently faces a cyber pandemic, with the UAE alone reporting an increase of at least 250% in cyberattacks last year.
BIOS Middle East has been helping organisations across the UAE, Saudi Arabia and other parts of the Middle East to improve their information security practices across their IT infrastructure. From endpoint devices to enterprise workloads, our BIOS Secured monitors your network, systems and data 24 hours per day, 7 days per week, 365 days per year, on-premise or in the cloud. BIOS Secured offers 10 benefits:
• Security information and event management
• Intrusion prevention and detection
• Application security
• Next-generation firewalls
• Endpoint protection
• Threat Hunting
• Data loss prevention
• Web proxy and URL filtering
• Vulnerability management
• File integrity monitoring
• Executive reporting
Find out how BIOS Secured can help your organisation bridge the security gap. For more information on endpoint and server security, download the Gartner report here.

