Cybercrime is on the rise and it’s important that each member of your organization realizes the importance of data security. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025.
In today’s post, we will discover how to develop a robust data security strategy to secure your business and prevent external attacks.
Read More
Topics:
Best System Integrator UAE,
salesforce partner uae,
Managed Services UAE,
best cloud provider UAE,
best managed service provider UAE,
cyber security middle east,
local cloud provider,
gcc cloud,
cloud provider saudi arabia
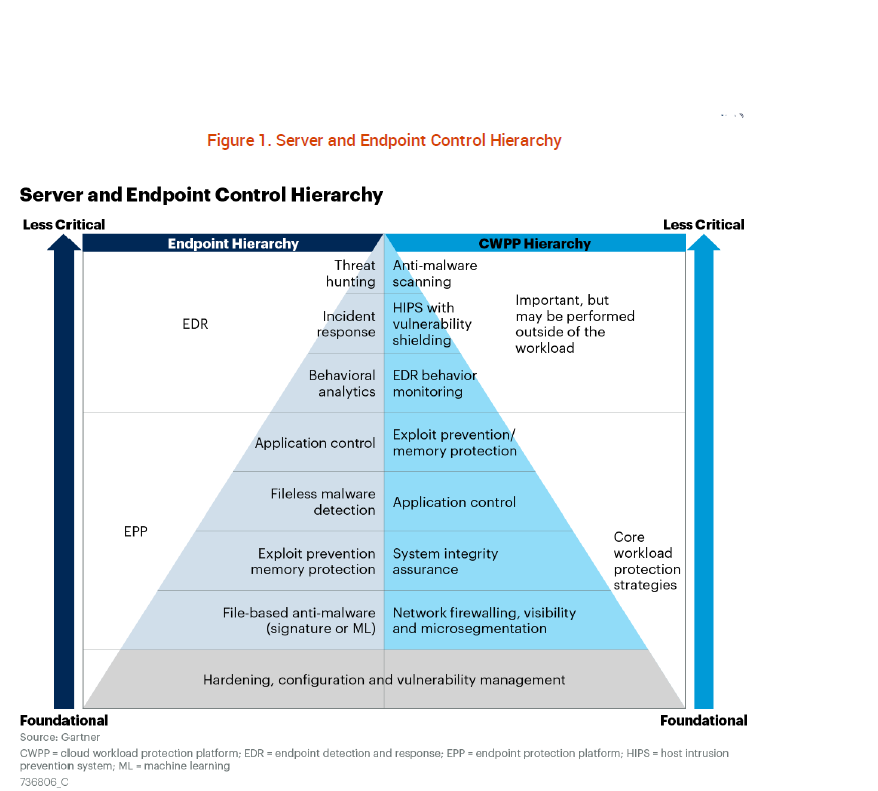
IT infrastructure has evolved considerably over recent years, but security considerations have remained static for many organisations. As first enterprise workloads have moved out of the organization to the cloud and then increasingly due to Covid, endpoints have moved from the office to the home, security remains largely focused on protecting the perimeter of the organization.
In addition, traditional servers have been transformed into Cloud workloads, containers and agile development apps platforms, however, it is still common practice to approach this new IT infrastructure with the same security solutions that are deployed for endpoint devices, according to a recent Gartner Report
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security middle east,
it security middle east,
it security companies,
security as a service,
security analysis',
siem,
bios secured
In the Middle East, as around the world, the coronavirus pandemic saw technology leaders tasked with maintaining business continuity in the face of work-from-home developments, data privacy threats and increased cyberattacks. 2021 could accelerate that trend.
With COVID-19 likely to continue shaping the immediate business ecosystem, CIOs will be entrusted with a greater share of the business. Technology leaders will be under greater pressure to deliver big results and performance metrics will be more closely monitored.
Accordingly, for Middle Eastern CIOs looking to stay ahead of the game in 2021, here are three tech-focused resolutions that are easy to implement and could win management appreciation.
Read More
Topics:
Managed Services UAE,
managed IT services UAE,
it services,
cyber security middle east,
bios secured,
Managed IT services Saudi Arabia,
Cloud Service Provider Saudi Arabia
The majority of IT security is traditionally focused on securing the corporate network
at the perimeter and the core. The new reality of working remotely due to COVID-19
means the game has changed. Hackers are less interested in bypassing corporate
firewalls now they know they can attack the endpoints much more easily and gain
access that way. In addition, now that all the users are outside of the network,
disrupting a company’s ability to work is as simple as filling up all their available
bandwidth at the data center.
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security,
it security middle east,
it security companies,
security as a service,
bios secured
Congratulations! Simply by contemplating a vulnerability scan, your organization is more prepared than a majority of organizations. A recent study by Tenable shows that only 48% of companies perform any kind of regular vulnerability scan whatsoever – and only 5% conduct rigorous practices. If you want to become part of that 5%, however, you have to do more than consider a vulnerability scanning program – you have to commit.
Here’s what you need to know:
Read More
Topics:
it security,
cyber security middle east,
it security middle east,
security analysis',
bios secured
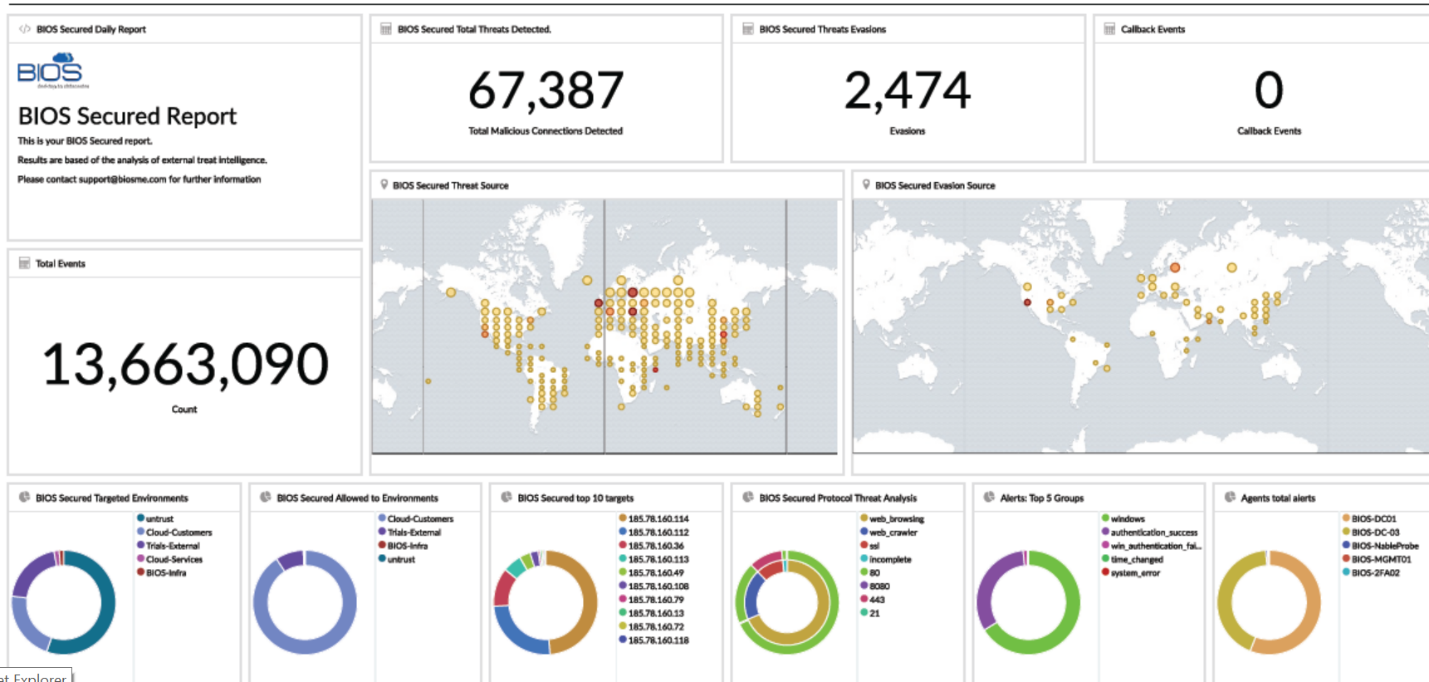
Ever since computers have been networked together, unauthorized access has been a concern. From the first viruses to modern-day cryptocurrency hacks, users have always needed to fend off cyber attacks. As computers have become a larger part of life and business, that concern has only grown, and rightly so. Major vulnerabilities are revealed with alarming frequency. Security holes like Meltdown and Spectre appear as if from nowhere, infecting huge numbers of systems and requiring immediate patches to close major vulnerabilities. Heartbleed undermined the security of OpenSSL, perhaps the largest secure communications protocol in the world. Critical Middle Eastern infrastructure was disrupted with the TRITON malware in December 2017, and 56% of the companies in the growing MENA market reported losing more than $500,
000 in cyber-attacks, according to PricewaterhouseCoopers’ 2016 report.
No business is immune from these kind of system vulnerabilities and attackers. As cyber crime become more sophisticated, how can you protect yourself—and your company—from cyber-attacks? The key is constant vigilance and appropriate security layers.
Read More
Topics:
cyber security middle east
You might think that your network is safe from attack. You might have even weathered the storm against ransomware or a DDOS a
ttack. But have you tried your luck against a determined, sophisticated attacker? A security gap analysis can help you find gaps in your network that attackers will capitalize upon, securing your netw
ork against penetration and exploitation. Whether you work with a third party to conduct the security gap analysis or run it on your own, you’ll follow the same basic steps.
Read More
Topics:
it security,
cyber security,
cyber security middle east
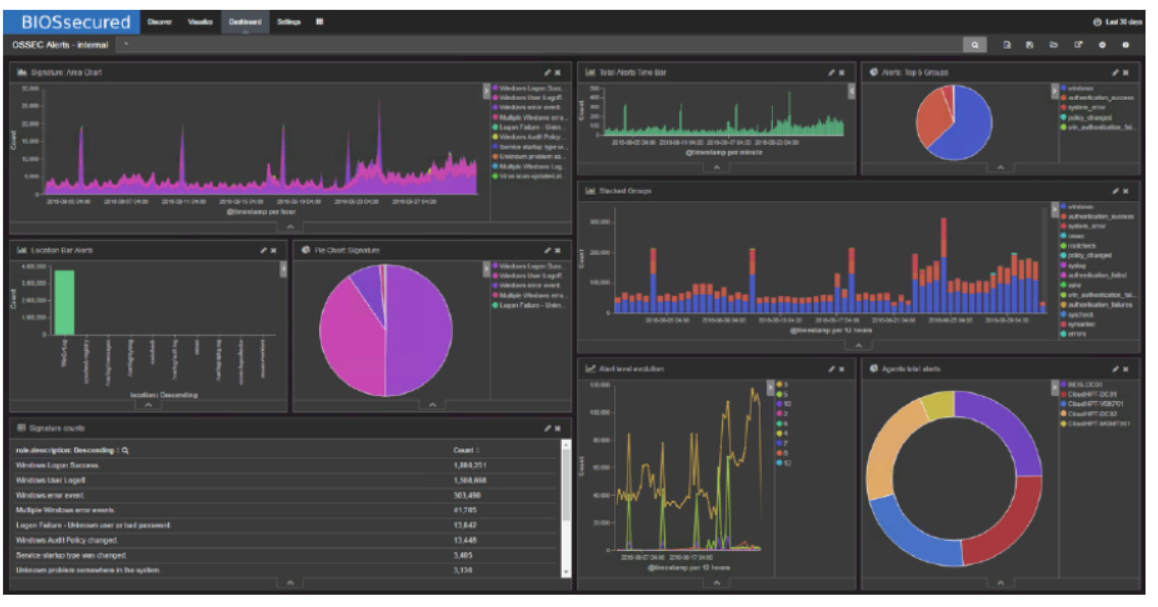
SIEM stands for Security Information and Event Management. It’s a complex web of technologies and software tools that provide real-time monitoring and reporting of large scale IT infrastructure. By hosting a centralized viewpoint for security event management, log collection and infrastructure alerts, IT teams and cyber security professionals can keep tabs on networks of any size.
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security,
network security middle east,
it security middle east,
it security companies,
security as a service