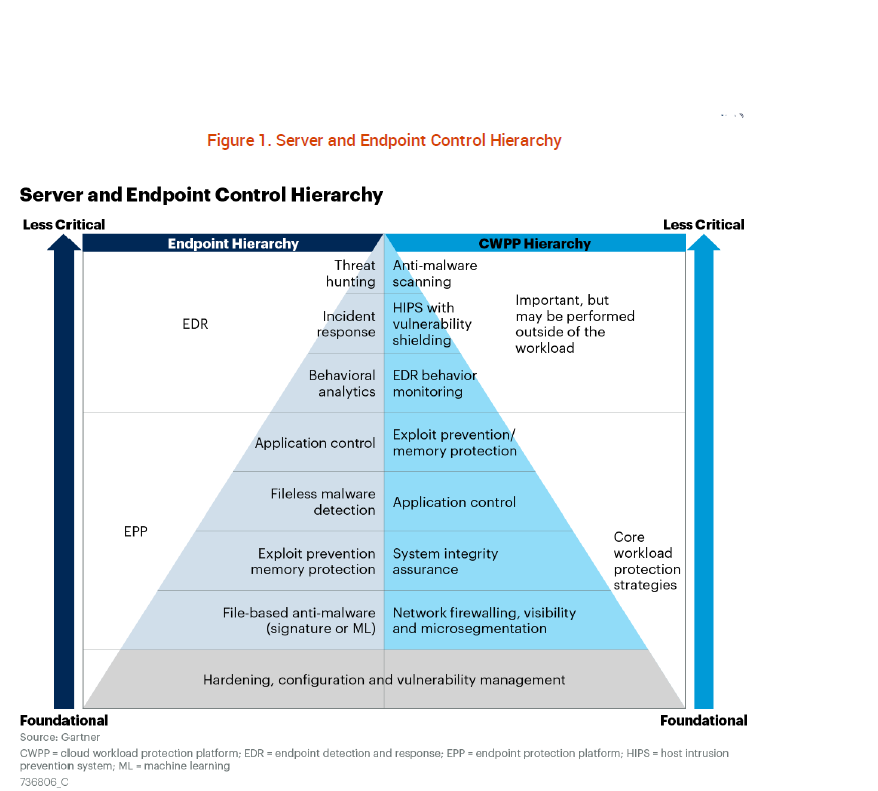
IT infrastructure has evolved considerably over recent years, but security considerations have remained static for many organisations. As first enterprise workloads have moved out of the organization to the cloud and then increasingly due to Covid, endpoints have moved from the office to the home, security remains largely focused on protecting the perimeter of the organization.
In addition, traditional servers have been transformed into Cloud workloads, containers and agile development apps platforms, however, it is still common practice to approach this new IT infrastructure with the same security solutions that are deployed for endpoint devices, according to a recent Gartner Report
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security middle east,
it security middle east,
it security companies,
security as a service,
security analysis',
siem,
bios secured
The majority of IT security is traditionally focused on securing the corporate network
at the perimeter and the core. The new reality of working remotely due to COVID-19
means the game has changed. Hackers are less interested in bypassing corporate
firewalls now they know they can attack the endpoints much more easily and gain
access that way. In addition, now that all the users are outside of the network,
disrupting a company’s ability to work is as simple as filling up all their available
bandwidth at the data center.
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security,
it security middle east,
it security companies,
security as a service,
bios secured
According to Gartner, “COVID-19 has disrupted operations and will have prolonged impacts on continuity of operations, modes of working and growth patterns. CIOs need to respond to the crisis with both short- and long-term actions to increase resilience against future disruptions, and prepare for rebound and growth.”
As businesses in the Middle East adjust to the new realities of operating during the COVID 19 pandemic, BIOS is committed to providing thought leadership information and solutions that can help our customers navigate these uncertain and difficult times.
Read More
Topics:
Cloud Provider UAE,
it security,
it security companies,
cloud and managed service provider,
cloud hosting,
combating COVID-19
Congratulations! Simply by contemplating a vulnerability scan, your organization is more prepared than a majority of organizations. A recent study by Tenable shows that only 48% of companies perform any kind of regular vulnerability scan whatsoever – and only 5% conduct rigorous practices. If you want to become part of that 5%, however, you have to do more than consider a vulnerability scanning program – you have to commit.
Here’s what you need to know:
Read More
Topics:
it security,
cyber security middle east,
it security middle east,
security analysis',
bios secured
You might think that your network is safe from attack. You might have even weathered the storm against ransomware or a DDOS a
ttack. But have you tried your luck against a determined, sophisticated attacker? A security gap analysis can help you find gaps in your network that attackers will capitalize upon, securing your netw
ork against penetration and exploitation. Whether you work with a third party to conduct the security gap analysis or run it on your own, you’ll follow the same basic steps.
Read More
Topics:
it security,
cyber security,
cyber security middle east
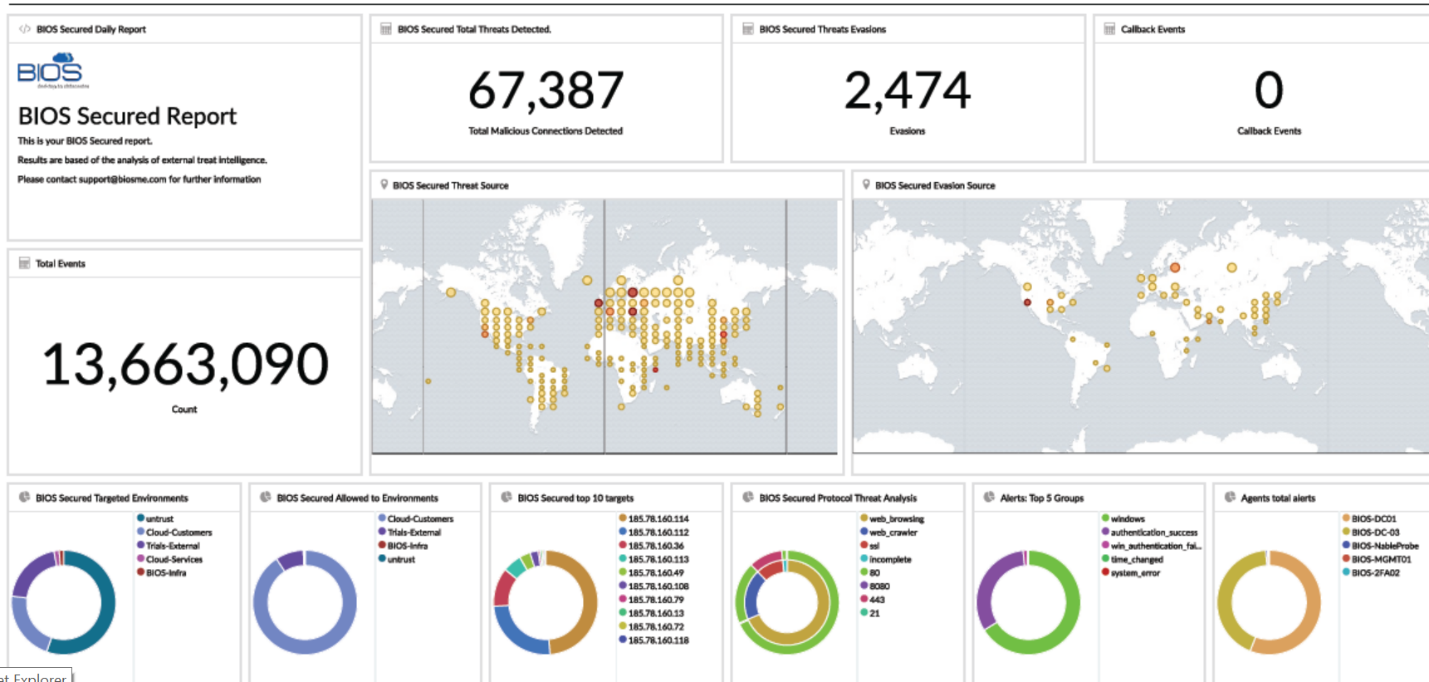
SIEM stands for Security Information and Event Management. It’s a complex web of technologies and software tools that provide real-time monitoring and reporting of large scale IT infrastructure. By hosting a centralized viewpoint for security event management, log collection and infrastructure alerts, IT teams and cyber security professionals can keep tabs on networks of any size.
Read More
Topics:
it security,
cyber security,
cyber security middle east,
network security,
network security middle east,
it security middle east,
it security companies,
security as a service
Information security handles the protection of digital privacy of critical data of businesses, organizations, and individuals. It includes various preventive methods for restricting unauthorized access to databases, systems, machines, and networks.
Security measures include but are not restricted to data backups, encryption, DLP planning, digital rights management, and more. This article discusses ten things that you need to be doing in 2017 to ensure your data is secure.
Read More
Topics:
online backup dubai,
IT Back Up,
online disaster recovery uae,
draas uae,
it security,
baas,
data protection